Retail SD-WAN & PCI DSS: A Technical Guide to Reducing Audit Scope via Segmentation
Traditional flat network architectures leave every device "in scope" for audit, creating compliance headaches and exposing payment data to lateral movement attacks. Find out how SD-WAN fixes that.

Retailer’s networks are now having to support everything from point-of-sale terminals to self-checkout kiosks, payment processors to inventory scanners, CCTV systems to guest Wi-Fi, as well as digital signage - and with PCI DSS v4.0 now in full effect since March 2025, retailers face stricter requirements around network segmentation and cardholder data environment (CDE) isolation than ever before. This means that traditional flat network architectures leave every device "in scope" for audit, creating compliance headaches and exposing payment data to lateral movement attacks.
In this article we’ll explore how SD-WAN can be essential for retail payment environments and how it can provide compliance benefits through reduced PCI audit scope on top of security benefits (such as breach containment across stores).
The Problem: The "Flat Network" Trap
One of the biggest issues with legacy retail networks is the assumption that once a device connects to the store network, it can be trusted, which doesn’t meet modern needs or requirements. This flat architecture not only means a customer connecting to guest Wi-Fi can theoretically "see" payment terminals on the same network segment but so can every other networked device that the retailer uses. If an attacker compromises a low-value target such as digital signage, they can gain a foothold for lateral movement within the network and work their way towards systems storing cardholder data.
From a compliance perspective, PCI DSS requires proper firewall configuration, network segmentation and penetration testing to validate segmentation effectiveness – as mentioned before, without proper segmentation, every device in your store falls within audit scope.
And there have been all new cost implications for PCI DSS v4.0, which, according to industry analysis, introduced 64 new requirements that all focus on continuous risk assessment, privileged access management and network segmentation. Given this expansion of audit scope, especially when considering non-payment systems, retailers face higher assessment costs and longer audit timelines more than ever.
The Solution: Macro-Segmentation vs. Micro-Segmentation
Whilst segmentation in itself is well-known, understanding the differences between macro-segmentation and micro-segmentation, as well as their inclusions within SD-WAN is far less known.
Macro-segmentation isolates entire locations from one another, leveraging Virtual Routing and Forwarding (VRF) to create logically separate networks over the same physical infrastructure. This means that if one store suffers a breach, the attack cannot propagate to another.
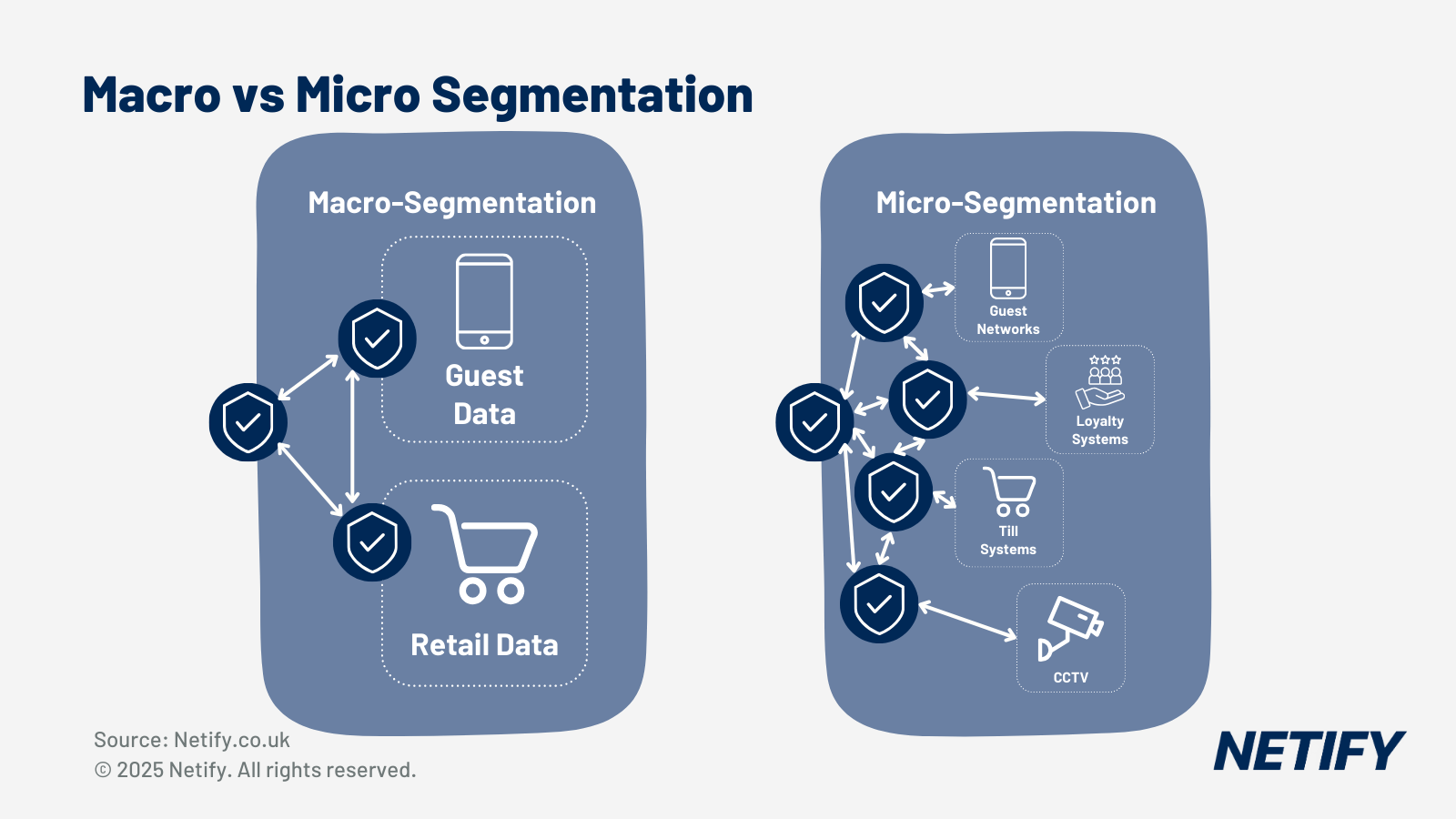
Micro-segmentation operates within individual stores, creating isolation between payment terminals, back-office systems, CCTV, guest Wi-Fi, digital signage and IoT devices. Rather than treating all in-store systems as equally trusted, micro-segmentation enforces strict access controls – for example, a compromised digital signage display cannot communicate with payment terminals because SD-WAN policies explicitly deny that traffic path.
It's therefore imperative to look at these as not competing technologies but layers of the same security stack, protecting each level of data in its own way to ensure maximum protection for the overall retail network.
The "CDE" (Cardholder Data Environment) Strategy
Establishing an effective CDE requires defining both which systems fall within scope and how traffic should flow between zones. The CDE encompasses all systems that store, process or transmit cardholder data, such as POS terminals processing transactions, payment gateways routing authorisations and card validation systems - with each component requiring explicit inclusion in segmentation policies based on its role in the payment flow.
CDE traffic control operates on an egress-only principle - payment terminals can initiate outbound connections to payment processors but no external systems can establish inbound connections into the CDE regardless of authentication state. This approach ensures that even if an attacker compromises systems in an adjacent network zone, they cannot leverage that access to initiate connections into the CDE, as all inbound traffic is denied by default (with no exceptions for non-payment services).
CDE architectures vary significantly across retail formats, such as with petrol stations where both outdoor pump terminals and indoor payment systems can potentially be tampered with. Alternatively at the likes of quick-service restaurants where they operate both self-order kiosks alongside traditional POS terminals at counters each configuration requires differing segmentation policies that reflect the specific payment flows and device use cases.
ASIC-Accelerated Inspection
Fortinet's approach centres on their SoC4 and SP5 ASIC processors, which handle deep packet inspection (DPI) at wire speed. This matters for retail because enabling security inspection on generic hardware introduces latency that can cause transaction timeouts, whereas the FortiGate platform delivers 10x higher performance, allowing full SSL/TLS inspection without impacting transaction processing times.
PCI DSS v4.0 Changes Relevant to SD-WAN
Given the changes present in PCI DSS v4.0, there are several impacts on the monitoring and testing of SD-WAN segmentation - for example, continuous monitoring replaces point-in-time assessment, where SD-WAN platforms must provide real-time visibility into segmentation effectiveness and requirement 11.4.6 requires annual penetration testing plus additional testing after any segmentation changes.
PCI DSS v4.0 risk assessments now evaluate the complete security posture of systems interacting with the CDE rather than treating network infrastructure as implicitly trusted. This extends Multi-Factor Authentication (MFA) requirements to all SD-WAN management interfaces that configure or access CDE systems - recognising that any compromised network infrastructure provides potential for lateral movement opportunities that can be considered equivalent to direct CDE access, with the SD-WAN management system now becoming part of the assessed security perimeter rather than excluded as supporting infrastructure.
Wireless and Guest Wi-Fi Controls
Software-defined banch architectures are increasingly being used within retail environments to allow for functionalities like guest Wi-Fi, however this comes with the requirement of multiple segmentation layers. Under new guidelines, it’s ideal that retailers implement several key controls.
First, guest networks need to be completely separated from your internal network - not just logically, but with hard blocks preventing any access to payment systems. Customers connecting to Wi-Fi should hit a login page (captive portal) before they can browse, and their devices shouldn't be able to see or communicate with other customers' devices on the same network.
For more sophisticated setups, technologies such as Private Pre-Shared Keys (PPSK) allow you to give different groups different access levels - staff might get one password whilst contractors get another with more restrictions. And whilst older WPA2 encryption is still common, WPA3 provides stronger protection against eavesdropping, which matters when customers are potentially accessing sensitive information over your network.
East-West vs. North-South Traffic
Traditional security architectures focus on north-south traffic entering and leaving the network, largely ignoring east-west traffic between internal systems and attackers often exploit this blind spot. Network segmentation research demonstrates that micro-segmentation that limits east-west traffic is key to significantly reducing attack success rates by eliminating lateral movement pathways.
SD-WAN platforms are ideal for this as they can enforce segmentation at the branch level to provide local east-west traffic control without requiring inspection at central data centres. This means that, when digital signage attempts to communicate with POS terminals within the same store, the SD-WAN appliance blocks traffic locally rather than allowing it to traverse the network for inspection elsewhere - reducing latency whilst enforcing isolation at the point where traffic originates.
Logging, Monitoring & Evidence for Auditors
When Qualified Security Assessors (QSAs) check to see if retailers are compliant with PCI DSS, they typically request specific evidence that demonstrates segmentation controls operate continuously rather than just during testing.
When considering SD-WAN platforms, retailers should consider how solutions provide per-zone traffic flow reports as it’s essential for compliance to be able to show allowed connections/denied attempts, blocked connection logs proving active isolation enforcement, topology views clearly identifying which systems fall within CDE scope and which sit outside it, alongside change management audit trails showing who modified segmentation policies with timestamps and justifications.
Hybrid CDE Architectures
In recent years, retailers have increasingly moved payment processing to cloud-hosted SaaS platforms rather than operating on-premises infrastructure, which introduces new segmentation considerations as the CDE spans both branch locations and cloud environments. SD-WAN segmentation policies must account for these cloud-based CDE components, restricting traffic from in-store payment terminals to specific cloud destinations over encrypted channels whilst preventing lateral movement between cloud services.
For example, when a customer taps their card at a retail terminal, the payment authorisation might flow through a cloud-hosted payment gateway, a SaaS POS application where the retailer doesn't control underlying infrastructure or a regional data centre operated by the payment processor.
SD-WAN segmentation policies must therefore account for these distributed CDE components - with traffic from in-store payment terminals restricted to specific cloud destinations over encrypted channels rather than permitting general internet access that attackers could exploit.
The PCI SSC's guidance emphasises that all segmentation controls must remain consistent across on-premises and cloud-hosted CDE components, with retailers demonstrating that cloud connectivity doesn't introduce lateral movement pathways between environments. For retailers using SASE architectures (SD-WAN with cloud-based Security Service Edge capabilities), SASE platforms can more-easily enforce consistent segmentation policies whether traffic flows between in-store systems, to cloud-hosted applications or to third-party payment processors, with the same security inspection applied regardless of destination type.
High-Level Design Patterns
How retailers connect their stores together has a big impact on both compliance and day-to-day operations. There are three main approaches, each with different implications for PCI DSS.
- Hub-and-spoke is the simplest setup from a compliance perspective. Every store connects back to headquarters, with no direct connections between stores. This makes life easier for PCI audits because cardholder data only travels in one direction - from store to HQ. The downside? Headquarters becomes the single point where everything can go wrong. If that connection fails, your entire estate can be affected.
- Full mesh takes the opposite approach - every store can talk directly to every other store. This is brilliant for operational flexibility, especially if you're running ship-from-store programmes where any location might fulfil an order. But from a PCI perspective, it's a nightmare. Because cardholder data could theoretically travel across any connection in your network, every link falls within audit scope. If you go down this route, you'll need rock-solid segmentation to ensure payment terminals can only use the mesh for legitimate payment processing - nothing else.
- Regional hubs offer a middle ground. Stores connect to regional data centres, which then connect to national headquarters. This gives you better performance than routing everything through a single central location, whilst keeping your security perimeter manageable. Regional hubs become natural enforcement points where you can apply extra security controls before traffic moves between regions or up to headquarters. For larger retailers, this often provides the best balance between operational needs and audit complexity.
Pre-Audit Network Review Checklist
1. CDE Isolation Verification: Run penetration tests from non-CDE systems attempting to reach payment terminals across different attack vectors: port scanning, protocol exploitation, application-layer attacks - with every attempt blocked and logged by SD-WAN segmentation policies rather than reaching target systems.
2. Guest Wi-Fi Segregation: Connect to guest Wi-Fi networks and attempt discovering internal systems through network scanning, ARP requests and DNS enumeration, verifying that guest devices can only reach internet gateways rather than internal network segments regardless of technique employed.
3. Segmentation Policy Documentation: Generate topology diagrams showing CDE boundaries and traffic flows, export complete policy rule sets with source zones, destination zones and permitted protocols, and document business justification for each allowed traffic flow rather than relying on default-permit rules inherited from legacy configurations.
4. Continuous Monitoring Evidence: Review SD-WAN logs demonstrating 24/7 segmentation policy enforcement with automated alerts for violations - showing that monitoring operates continuously rather than only during audit preparation periods, with alerts triggering investigation procedures rather than just logging events.
5. Administrative Access Controls: Verify Multi-Factor Authentication (MFA) for all SD-WAN management access regardless of source network, implement least-privilege access for administrative accounts rather than shared credentials with full permissions, and maintain comprehensive change audit trails showing who modified segmentation policies, when changes occurred and what justifications supported modifications.
Conclusion
PCI DSS v4.0's emphasis on continuous monitoring, penetration testing and targeted risk assessment makes network segmentation essential rather than optional for retailers processing card payments. SD-WAN provides the granular policy enforcement, logging and automated monitoring that v4.0 demands, whilst accommodating modern retail operations and the nuances of different retailer-type’s needs.
For retailers still operating flat networks or legacy MPLS infrastructure without proper segmentation, the transition to SD-WAN is ideal for minimising operational disruption, reducing audit preparation burden through continuous compliance rather than annual exercises and avoiding the risk of leaving systems within CDE boundaries.

Harry holds a BSc (Hons) in Computer Science from the University of East Anglia and serves as a Cybersecurity Writer here at Netify, where he specialises in enterprise networking technologies. With expertise in Software-Defined Wide Area Networks (SD-WAN) and Secure Access Service Edge (SASE) architectures, Harry provides in-depth analysis of leading vendors and network solutions.
Fact-checked by: Robert Sturt - Managing Director, Netify
Frequently Asked Questions
How does SD-WAN segmentation reduce PCI DSS audit scope?
SD-WAN creates hard boundaries between the CDE and non-CDE systems. When properly implemented, retailers can exclude entire categories of devices from audit scope because segmentation policies prevent these systems from accessing the CDE, reducing assessment costs and remediation effort.
What's the difference between macro-segmentation and micro-segmentation?
Macro-segmentation operates at the location level, isolating entire stores from each other using VRF or VPN overlays. Micro-segmentation operates within individual stores, creating isolation between different system types on the same site. Both layers work together to limit lateral movement and reduce audit scope.
Do cloud-hosted payment systems need to be included in the CDE?
Yes. When retailers process payments through cloud-hosted SaaS platforms, those cloud systems become part of the CDE. SD-WAN segmentation policies must account for connectivity between in-store payment terminals and cloud-hosted CDE components, ensuring only authorised payment applications can reach these services.
How frequently must retailers test SD-WAN segmentation controls?
PCI DSS v4.0 Requirement 11.4.6 mandates annual penetration testing of segmentation controls, plus additional testing after any changes to segmentation methods. Beyond formal testing, v4.0's continuous monitoring emphasis means retailers should implement automated segmentation validation rather than relying solely on annual assessments.
