Leveraging SASE to Detect Lateral Movement and Insider Threats
Businesses that utilise hybrid networks often have blind spots where lateral movement and insider threats can go undetected. However, through SASE’s unification of networking and security, these businesses can enforce identity-driven access control.

If you're running a hybrid network your business will typically cater to users that work from home, branch offices or even from coffee shops – not all of which you can control the security posture of. Often times, applications are scattered across clouds and ‘your infrastructure’ may actually be rented from a data centre, unlike traditional setups where everything was in-house, with security teams monitoring everything passing through a fixed perimeter. Instead, nowadays, threats move silently through these environments due to the shift in where security is applied.
This article explores how SASE (Secure Access Service Edge) is essential for threat detection, especially in cloud or hybrid use cases by unifying networking and security into a single cloud-delivered framework.
Understanding Lateral Movement and Insider Threats
What is Lateral Movement?
Lateral movement happens when an attacker compromises an initial entry point, such as a user's credentials or a branch device and then utilises that point to quietly move through your internal network to access higher-value assets. Given they may not immediately strike lower-value assets, with traditional security solutions they may remain entirely undetected until it’s too late and high-value or sensitive information is exfiltrated.
What are Insider Threats?
Similarly dangerous, insider threats are different in nature but can also go undetected with traditional security methods. A malicious employee, disgruntled contractor or compromised internal account can abuse their legitimate access to steal data, create backdoors or sabotage systems. Unlike external attackers, insiders already have access, bypassing perimeter-style security.
Why it’s difficult to protect against both
Both of these threats exploit the same gap in traditional network architectures in that they assume that once someone or something is inside the perimeter, it's trustworthy. Unfortunately, this just isn’t the case in modern systems, especially when considering the likes of cloud-first architectures.
For example, when your applications live in multiple clouds, your users bypass traditional network paths and old-style perimeters disappear entirely.
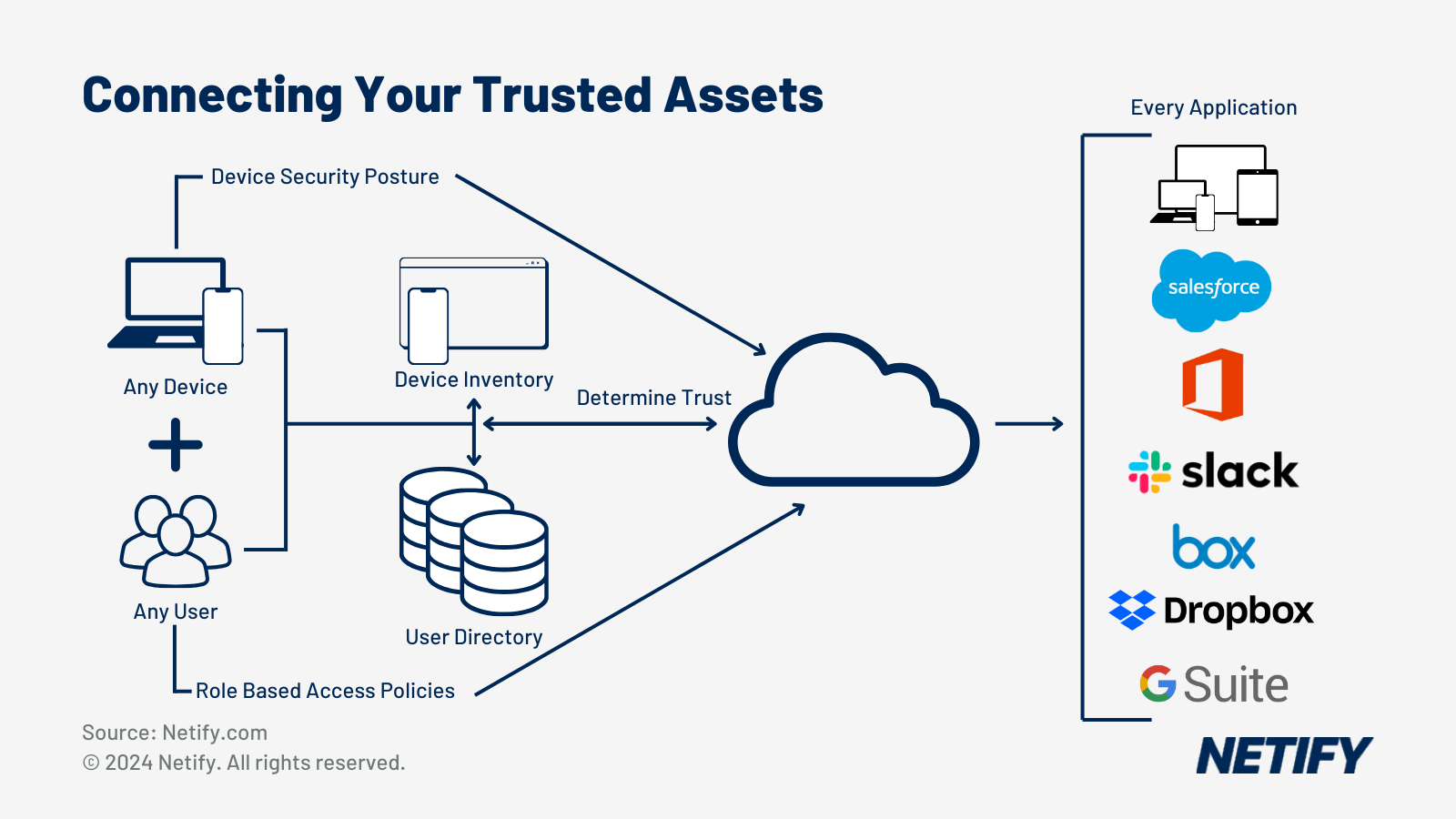
On top of this, traditional security tools compound the problem, with firewalls often only inspecting traffic crossing network boundaries (north-south traffic), which can leave east-west communication between internal systems largely unmonitored. Furthermore, access controls are often left static, access to resources is typically granted once and that access persists regardless of context. These issues help facilitate lateral movement and rely primarily on the trust placed on credentials without any form of further authentication or verification.
How SASE Eliminates Blind Spots Through Unified Architecture
To combat the blind spots of traditional architectures, SASE inspects all traffic regardless of user location, device type or application destination. With SASE being cloud-delivered, all network functions (be it routing, policy enforcement or firewalls and web gateways) can be delivered from a single centralised point – ensuring unified inspection across all network traffic.
Instead of trusting devices once they connect, SASE implements identity-driven access control. Every user, device and application interaction is verified against identity, device health, location and behaviour to ensure all aspects are as expected – with access decisions reflective of this, not being permanent and adapting in real-time to the context of the connection.
Any risky behaviour detected can therefore be immediately evaluated against policies and an anomalous access pattern, regardless of where it came from, can then be investigated to prevent insider threats and lateral movement.
The SASE Framework: Key Components for Threat Detection
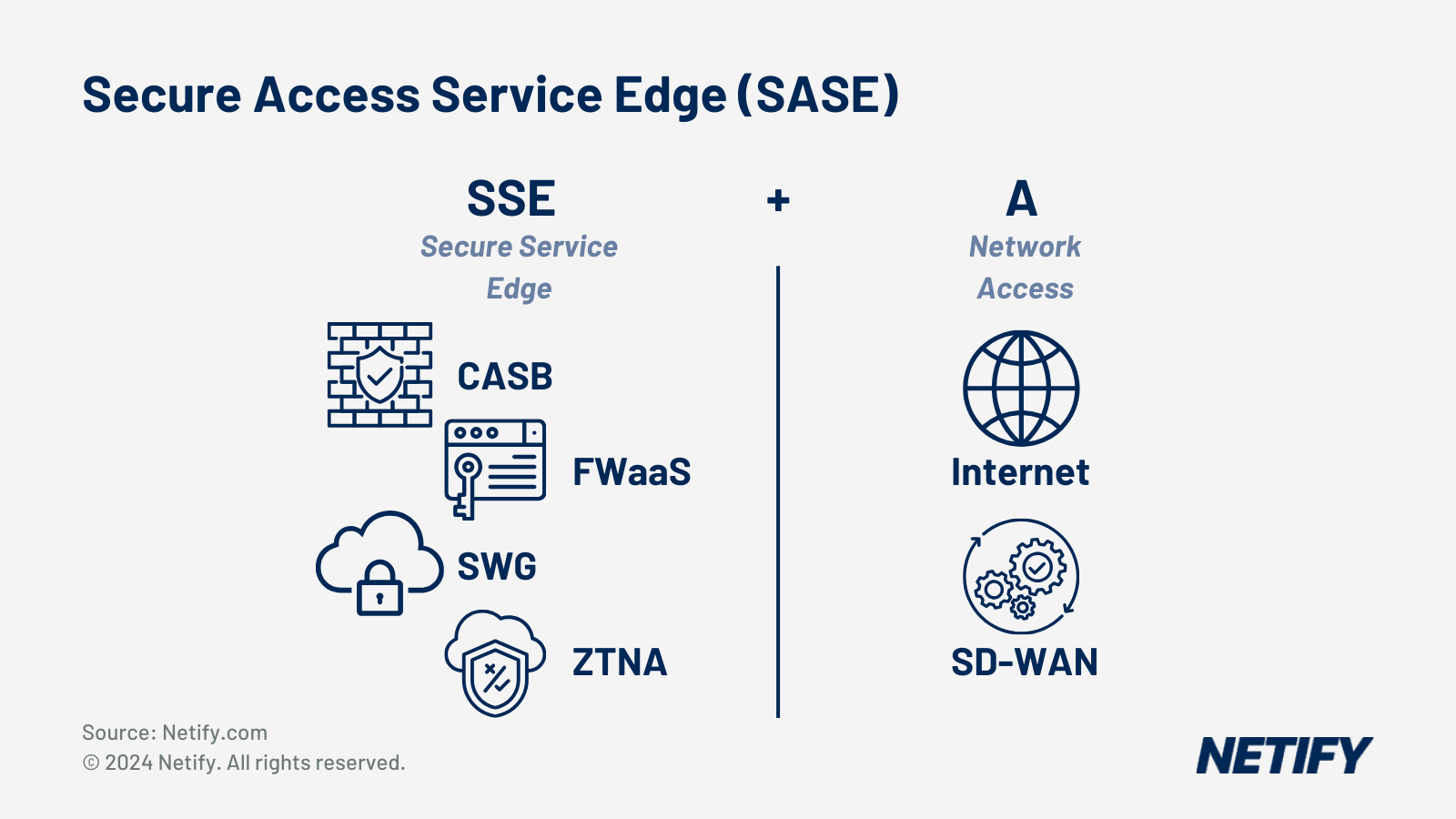
SASE is built upon five core capabilities working together, each offering their own facet of threat detection:
How SASE utilises SD-WAN Integration
SD-WAN is the networking component of SASE, routing traffic to the closest security processing point, with every route running through SASE inspections before reaching its destination.
How SASE Detects Lateral Movement
Segmentation Methods
- Identity-based segmentation stops attackers from moving freely - the compromised user's account can only access applications and resources aligned to their role. When the attacker attempts to access a database or system outside that user's normal permissions, ZTNA denies the request, whilst SASE logs the attempt and flags it as anomalous.
- Micro-segmentation reduces internal attack pathways - rather than assuming all systems on an internal network can talk to each other, SASE restricts communication to specific, policy-defined paths, preventing communications to systems that should be out of scope for users/applications.
- Cloud-based inspection flags unusual internal communication in real time. An attacker probing systems for vulnerabilities generates traffic patterns completely different from normal business activity and SASE’s FWaaS components can detect these scanning attempts. For example, a user's account suddenly connecting to administrative systems it has never accessed, from a branch device that normally only accesses specific applications, gets flagged immediately.
Finally, SASE congregates all detected activity into a single dashboard for a unified security overview. This could result in one alert for identity anomalies, another for device health concerns, a third for unusual network traffic and fourth for application-level access requests – all of which can help your security team or network administrators determine what's actually happening and where the source of issues are.
Detecting Insider Threats Through SASE
Insider threats are typically far trickier to detect because the attacker has legitimate access, with difficulties only growing due to remote work patterns leading to workers that are no longer seen in-person either. This has meant that the traditional methods of defence against insider threats weren’t about preventing access but merely damage limitation. However, through SASE’s handling of insider threats, we can implement access prevention methods as well as damage limitations.
Behavioural deviations trigger adaptive policies - SASE builds a baseline of normal behaviour for each user and device. This allows detections when deviations occur, such as accessing applications outside normal hours, connecting from unusual locations or attempting to access data outside typical scope, with policies adapting to counteract these. Some of these counter measures can include additional verification (to ensure the user is who they say they are), session monitoring (to determine exactly what they are doing) and denying or removing access (often based on multiple indicators of high-risk).
SaaS monitoring catches the most common insider threat vector - When an employee suddenly downloads hundreds of files from shared repositories, a contractor gains access to systems beyond their project, when someone enables unusual forwarding rules in cloud email or even when data gets mass-uploaded to personal cloud storage - CASB components see these in action and alert security teams to investigate and intervene.
Correlating multiple factors reveals threats - By converging multiple systems into one, SASE is best placed to correlate multiple factors together and find the source of a threat as well as prevent. SASE correlates identity, device, location and timing to highlight genuine threats, reducing false positives that can become problematic when bolting on multiple layers of security to traditional operations.
Real-World Scenarios Where SASE Makes a Difference
Use Case 1: Stopping a Compromised Remote User
A remote user in Manchester clicks a malicious link. The attacker gains their credentials. In a traditional network, the attacker quietly accesses internal systems from the user's compromised laptop for weeks. With SASE, the attacker attempts accessing new internal systems outside the user's normal role. ZTNA denies access. FWaaS flags the unusual traffic. SWG logs suspicious outbound communication. The attack is disrupted before meaningful lateral movement occurs.
Use Case 2: Detecting Shadow Cloud Storage
A branch user uploads sensitive files to an unsanctioned cloud storage account. SWG detects the unusual outbound connection and large data transfer. CASB monitors what happens to those files. If they're accessed from unusual locations, if they're shared outside the organisation, the system flags it. Rather than discovering data loss months later from a ransom demand, the incident is caught in real time.
Use Case 3: Discovering Contractor Privilege Expansion
A contractor supporting your cloud migration gains access to migrate workloads. Unnoticed, they also gain access to databases, identity systems, and backup infrastructure - far beyond their project scope. ZTNA micro-segmentation prevents access to systems outside their designated scope. When they attempt to access systems they shouldn't, the attempt is denied and logged. CASB monitors unusual application access patterns. The privilege escalation is discovered immediately, not after they've had months of access.
Why SASE Is Becoming Essential for Modern Defence
The convergence of networking and security in SASE eliminates the exploitable gaps that traditional architectures leave open and with lateral movement requiring these blind spots to move through, SASE minimises this attack components. On top of this, insider threats require exploiting inconsistency between security systems and with SASE your business can enforce consistency across all edges helping to minimise these too.
Evaluating SASE Solutions for Your Organisation
When you're assessing SASE platforms, consider these capabilities:
- Strong identity integration - The system should connect with your identity provider, support multi-factor authentication natively and allow adaptive access policies based on identity context.
- Deep visibility into application and device context – Enables you to see what's happening at the application level, not just network level. Device health, user behaviour and any anomalies should all be visible through the management interface.
- Unified policy engine across SD-WAN and cloud security - Policies shouldn't be different for different edges. A user accessing an application should experience consistent security posture whether they're at headquarters, a branch office or remote.
- Global PoP network - Your SASE provider should have enough edge locations that traffic reaches inspection points within a reasonable latency. Too few PoPs mean performance degradation and potential security gaps due to time outs.
- Analytics and logging - A key element of your security understanding, these capabilities are needed for detailed audit trails, correlation across security functions and revealing threats.
Conclusion
Lateral movement and insider threats aren't new risks, however cloud-first and hybrid-work architectures have made them harder to detect with traditional perimeter-based tools. SASE helps minimise these issues through proactive threat detection by unifying security functions around a consistent identity and policy framework.
Rather than assuming "inside the network" is safe, SASE continuously verifies every access request and rather than detecting threats after lateral movement has occurred - SASE stops attacks at the attempt stage.

Harry holds a BSc (Hons) in Computer Science from the University of East Anglia and serves as a Cybersecurity Writer here at Netify, where he specialises in enterprise networking technologies. With expertise in Software-Defined Wide Area Networks (SD-WAN) and Secure Access Service Edge (SASE) architectures, Harry provides in-depth analysis of leading vendors and network solutions.
Fact-checked by: Robert Sturt - Managing Director, Netify
One app to build and publish your personalised SD-WAN & SASE Network Security RFP with AI support
Over thirty curated SD-WAN & Network Security vendors & providers can respond directly to your RFP, get AI-scored comparisons, message instantly, book demos, provide proofs of concept, and supply global Internet connectivity pricing for a complete end-to-end business case.
Try our free RFP BuilderFrequently Asked Questions
How does SASE detect lateral movement?
SASE detects lateral movement by using FWaaS to filter east-west traffic and ZTNA to enforce micro-segmentation, preventing attackers from pivoting freely between systems. When a user attempts to access systems outside their normal role, SASE denies access immediately and logs the attempt as anomalous.
Can SASE prevent insider threats?
Yes. SASE prevents insider threats by using CASB to monitor for behavioural deviations, such as mass downloads or access from unusual locations, and applying adaptive policies that require additional verification or block access entirely. It correlates identity, device health, and access patterns to identify genuine threats while reducing false positives.
Why is traditional security insufficient for hybrid networks?
Traditional tools are siloed and rely on perimeter trust, leaving blind spots that fail to monitor traffic once it is 'inside' the network. When applications, users, and workloads are distributed across clouds, branches, and remote locations, the traditional perimeter disappears entirely. SASE replaces perimeter-based trust with continuous, identity-centric verification everywhere.
What is the difference between SASE and SD-WAN?
SD-WAN optimises network routing and performance, but SASE combines SD-WAN with integrated cloud security (ZTNA, SWG, CASB, FWaaS). SASE ensures every traffic path - regardless of routing destination - passes through unified security inspection. This creates consistent threat detection across all edges, whereas traditional SD-WAN alone has no built-in security guarantee.
How does SASE handle performance for global organisations?
SASE uses a distributed cloud architecture with multiple Points of Presence (PoPs) globally. Traffic is routed to the nearest PoP for inspection, reducing latency and bandwidth consumption compared to traditional architectures that backhaul all traffic to a central security point. This allows security inspection without performance degradation.
Is SASE suitable for small or mid-sized businesses?
Yes. SASE is cloud-delivered, so there's no on-premise hardware to manage or maintain. Small to mid-sized businesses benefit from enterprise-grade security without the operational overhead and can also utilise managed service providers to mitigate any issues with lack of expertise.
