AES (Advanced Encryption Standard)
Advanced Encryption Standard is one of the most secure encryption algorithms available globally - typically used when protecting sensitive data.

The Advanced Encryption Standard (AES) is a popular encryption algorithm that is widely used for data security. It is one of the most secure encryption standards available and has been adopted by various organisations and industries globally for safeguarding sensitive data.
AES is a symmetric encryption algorithm, implying that the same key is used for both encryption and decryption of the data. It functions by dividing the plain text into 128-bit blocks and utilising mathematical operations on each block, using a secret key. The resulting cyphertext is then stored or transmitted and can only be decrypted using the same secret key that was used for encryption.
One of the critical features of AES is its ability to offer various key sizes, including 128-bit, 192-bit, and 256-bit keys. Even if someone intercepts the encrypted data, it would take an enormous number of key combinations to break the encryption. It is estimated that cracking a 256-bit AES key would require millions of years, even with the most advanced computing technology available today.
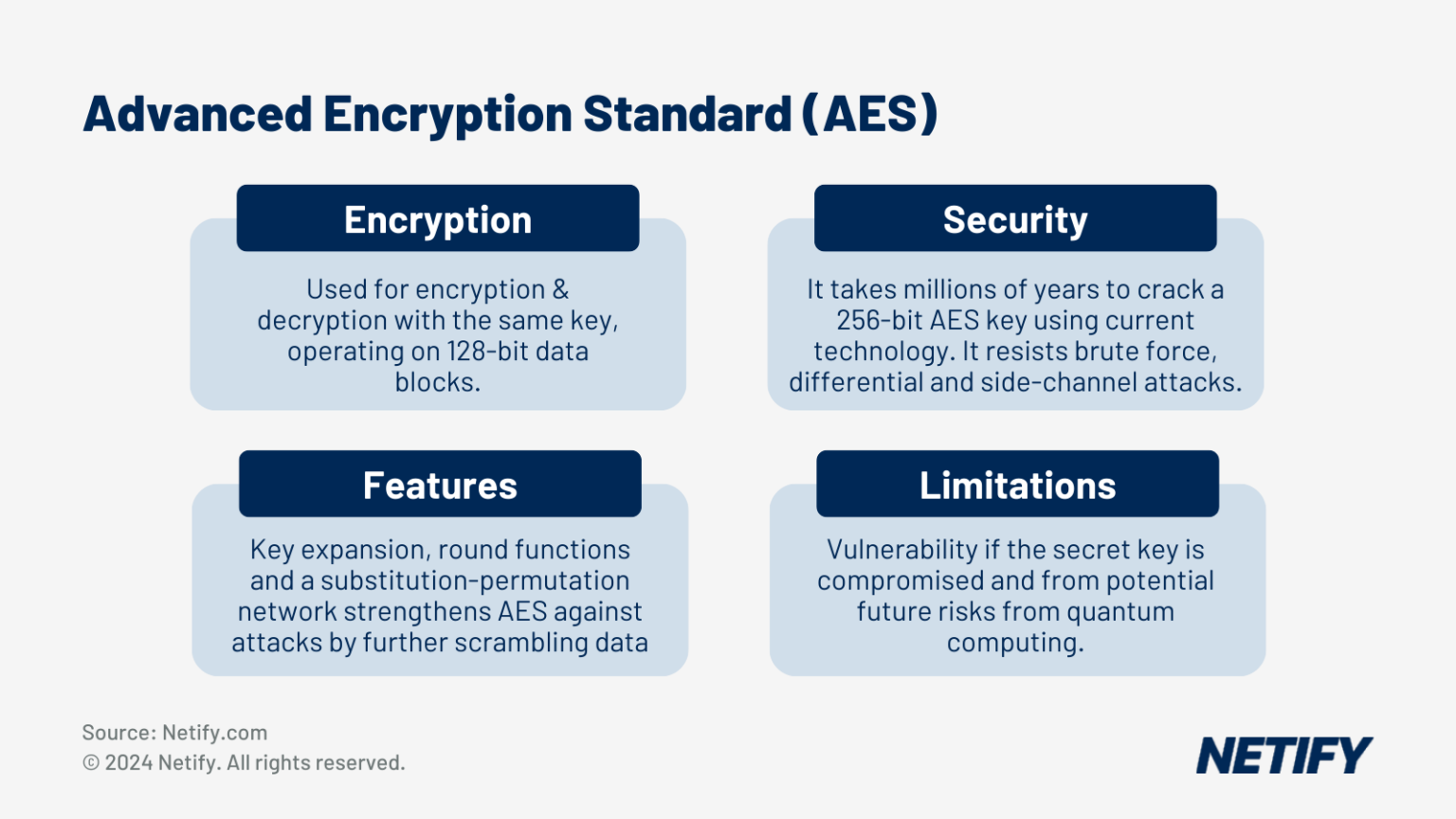
Another advantage of AES is its capability to resist various types of attacks, such as brute force attacks, differential attacks, and side-channel attacks. Brute force attacks require trying every possible key combination until the correct key is discovered, while differential attacks aim to identify flaws in the mathematical operations used in the algorithm. Side-channel attacks entail examining the power consumption or electromagnetic radiation emitted by a device during encryption, in order to infer information about the key being used.
To counter these attacks, AES incorporates several security features, including key expansion, a round function, and a substitution-permutation network. Key expansion generates a sequence of subkeys from the original secret key, which are then used in each round of the encryption process. The round function involves several mathematical operations applied to each block of plaintext and cyphertext. The substitution-permutation network uses a combination of substitution and permutation operations to further scramble the data.
In summary, AES encryption is an effective and widely used encryption standard that provides exceptional security for sensitive data. By understanding the technical workings of AES and its various strengths and limitations, organisations can make informed decisions about the best encryption techniques to use for their specific requirements.

Robert Sturt is a leading expert in SD-WAN and enterprise network solutions with extensive experience in telecommunications and network infrastructure. As a Forbes Business Council member and contributor to TechTarget, he provides strategic insights on network transformation and digital connectivity solutions. His expertise spans SD-WAN implementation, network security, and enterprise digital transformation initiatives.
Fact-checked by: Harry Yelland - Cybersecurity Writer, Netify
