Software Defined Perimeter
Software Defined Perimeter (SDP) is a security framework designed to dynamically created connections between the network perimeter and each user/device.
Software-Defined Perimeter (SDP) is a security framework designed to dynamically create individual connections between the network perimeter and each user/device. Developed by Cloud Security Alliance (CSA) in 2013, SDP addresses the limitations of traditional WAN network security, creating a more adaptable solution for working within a cloud-centric, mobile environment.
Traditional WAN networks use a perimeter-based security model, leveraging firewalls and VPNs in order to protect the network, however SDP offers a more adaptive solution. Software-Defined Perimeter operates at both the network and application layers of the network and hides the internal network infrastructure from unauthorised users. This minimises network visibility and requires SDP to authenticate and authorise access via user identification and device posture prior to visibility being granted. This increases the network security by reducing the attack surface, offering granular context-aware access control and enables secure remote access to resources whilst preventing exposure of resources to the entire network. Due to this, SDP offers improved scalability and flexibility for networked environments.
Core Components of SDP
There are 4 core components of Software-Defined Perimeter architecture. These include the: Controller, Gateway, Client and Single Packet Authorisation and enable Zero Trust networking principles to be used to protect network resources.
Controller
The controller authenticates and authorises SDP clients and gateways, whilst tracking infrastructure in real-time. Through network administrators defining and managing access policies, the SDP controller can issue time-bound tokens to authenticated clients containing their access entitlements, provided that the client identification and device context match the policies. After SDP clients connect to the controller for authentication and authorisation, the received token enables the client access entitlements to the specific network location of requested resource gateway only.
SDP’s Role in Zero Trust Architectures
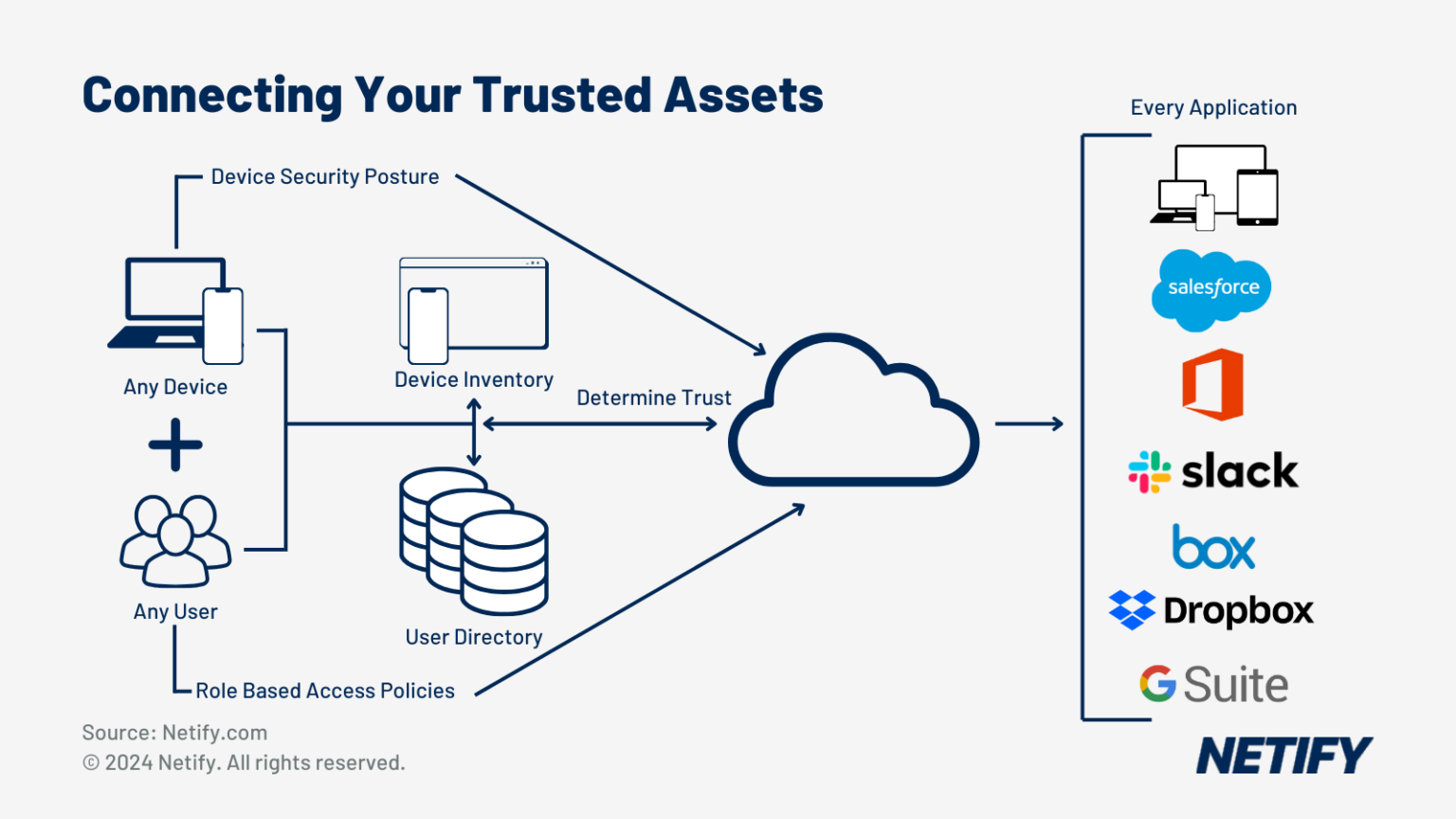
SDP is an essential security component of Zero Trust networking architectures. As SDP ensures access to resources is entirely limited and granted based on dynamic policy enforcement and continuous verification, this aligns with Zero Trust Network Access (ZTNA) principles. The shift away from traditional network firewalls allows user-centric and application-centric models, which form a key aspect of ZTNA.
The core principle behind ZTNA is ‘Never Trust, Always Verify’, where there is never implicit trust for any given user, device or network and each connection must be verified before network access is granted. SDP enables infrastructure to become invisible to outsiders, creating a ‘Darknet’ of IPs which are never exposed to the internet and hides resources from unauthorised users. By dynamically creating and securing the perimeter for each request, access can be granted based on granular policies and least privilege access. This means that connections can only be made to the specific application, not the entire network and prevents lateral movement across the network.
Advancements in SDP Technologies
One of the included improvements of version 2.0 was tighter integrations with Zero Trust frameworks, which were more commonly directly referencing SDP as a key architecture component. Updated specifications highlighted how SDP architecture enables organisations to implement core Zero Trust principles such as least privilege access, always assuming a breach and continuous verification.
Another improvement was that SDP 2.0 provided more details for the onboarding and access process. By elaborating on the roles of the SDP controller, accepting hosts and initiating hosts within each workflow, it assists in how components of SDP are deployed and how initiating hosts can obtain access to protected resources.
Finally, improved definitions of SPA were included. This provided more details on SPA message formats, the use of UDP and potential alternate transportation and discussions of the handling of Internet of Things (IoT) devices within an SDP environment. These discussions indicate how granular and dynamic access policies can be adapted to suit IoT.
SDP Deployment Models
SDP offers several deploy models for different network requirements, allowing organisations to leverage cloud, on-premises or hybrid architectures.
SDP Deployment Models
Security Benefits of SDP
Software Defined Perimeter minimises the attack surface of the network by hiding entry points to resources and preventing access to unauthorised users. Granular access control provides strict entry control criteria and limits potential damage that can be caused through compromised accounts. Additionally, through minimising network visibility, this also helps prevent distributed denial of service attacks.
These measures reduce the need for dedicated security appliances and can therefore improve the cost efficiency of network security. Through a central management system, SDP can also simplify management of scalability, creating greater security flexibility and easier secure integrations with the cloud.
Challenges and Considerations
Integrating SDP within existing systems can be challenging. This is due to systems using differing protocol standards, interfaces or outdated interfaces in the case of legacy systems. Cloud-based solutions may provide vastly different interfaces to on-premises applications and there these are important to consider and plan around prior to integration.
Granular control policies alongside additional security measures should be considered to protect against man-in-the-middle attacks. These attacks intercept traffic and pretend to be authorised users using the users verified connection. This can be mitigated through strong authentication and authorisation protocols to ensure that users, devices and connections are constantly being re-authenticated.
Future Directions and Industry Adoption
Software Defined Perimeters are being increasing used by various sectors, including finance, healthcare and government services. This is due to the enhance security capabilities offered by hiding network resources as it protects sensitive data and assists in regulation compliance. With the rise of remote working, SDP has become more favoured over traditional VPN methods due to access controls that SDP provides.
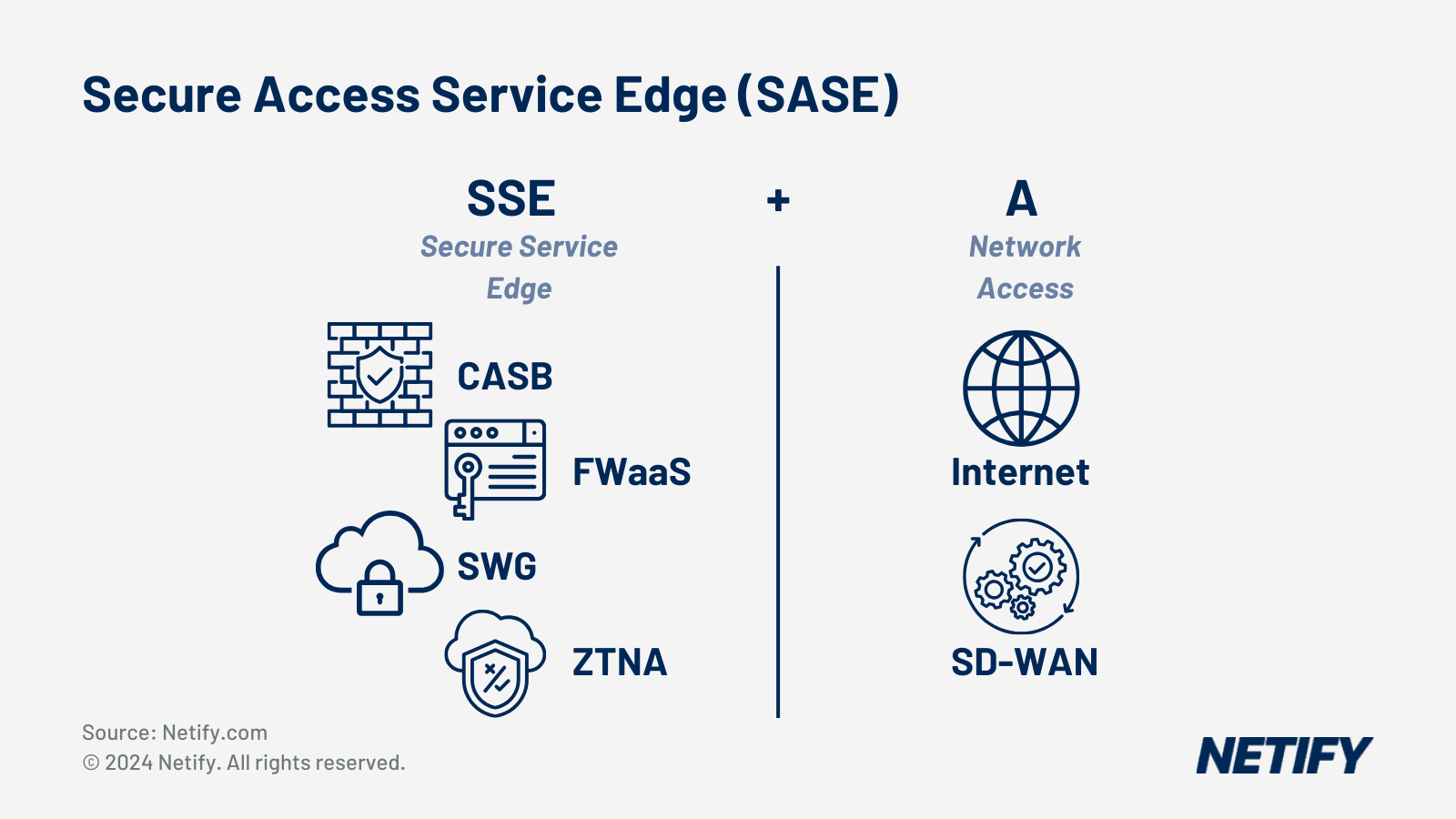
SDP is expected to become integrated into SASE frameworks to enhance cloud security. Another expectation is that Artificial Intelligence (AI) will be used for dynamic threat management. These integrations will improve overall network security.
Case Studies and Real-World Applications
A healthcare provider used SDP to ensure secure access to patient data across hospitals and remote care facilities. The solution was essential for enforcing compliance with health data protection regulations such as HIPAA. In environments where data sensitivity is high, SDP's ability to dynamically control access based on user context and risk assessment is vital.
Conclusion
Software Defined Perimeter hides network resources from unauthorised users, minimising the attack surface of the network and enhancing overall network security. SDP offers a solution for cloud, on-premises and hybrid environments, addressing the limitations of traditional WAN networks. These improvements enables businesses in finance, healthcare and government service sectors to comply with regulations and future directions indicate that SDP will increase its use cases through integrations with SASE and dynamic threat management through AI.

Harry holds a BSc (Hons) in Computer Science from the University of East Anglia and serves as a Cybersecurity Writer here at Netify, where he specialises in enterprise networking technologies. With expertise in Software-Defined Wide Area Networks (SD-WAN) and Secure Access Service Edge (SASE) architectures, Harry provides in-depth analysis of leading vendors and network solutions.
Fact-checked by: Robert Sturt - Managing Director, Netify
